Cybersecurity has a lot to do with everyone. Contrary to popular belief, it refers to more than keeping passwords safe, maintaining computers and keeping networks operational. Information security affects people in all countries and across all user groups and requires all their involvement.
Security affects families and kids and how they are kept safe in the online world and taught to make smart choices online so that they are not exposed to cyberbullying, viruses, spyware or worse. It is political when hacking and information breaches are motivated by nationalism, ideology and terrorism. It also affects business through data interception, malicious software and identity theft that can shut companies down and prevent customers from buying.
The statistics
Consider a few highlights from the Identity Theft Resources Center on data breaches reported in 2015. It records 781 reported breaches and more than 169 million records in which individual private information was lost or stolen in a data breach.1
These numbers refer to breaches reported by companies operating in the U.S. Many businesses did not report how many records were compromised, so the figure is understated. In the business category, 312 breaches involved more than 16 million reported records exposed:
- T-Mobile/Experian – 15 million records exposed
- Uber – 50,000 records exposed
- Sally Beauty Supply – 62,210 records exposed
- The Office of Jeb Bush – 13,000 records exposed
All this pales in comparison to medical healthcare, which saw 277 breaches involving more than 112 million reported records:
- UCLA Healthcare – 4.5 million records
- Premera Blue Cross – 11 million records
- Anthem – 78.8 million records
Ponemon Institute, an independent research group, estimates that the cost of a single data breach is $3.8 million with the cost linearly related to the time it takes to identify and contain the data breach incident.2 However, companies are increasingly challenged with knowing when they have been breached. According to the latest annual M-Trends report from cybersecurity company Mandiant, the median time from when a hacker gets on a network to detection is 146 days. Only 47 percent of companies discovered the breach themselves; 53 percent were notified by a third-party such as law enforcement.3
Overlooked in all these statistics is the present danger to physical infrastructure such as the electrical power grid and sewage treatment plants. Using search engine SHODAN, it is trivially easy to find equipment using Supervisory Control and Data Acquisition (SCADA), traffic lights, webcams, routers with default usernames/passwords as admin/1234, red light enforcement cameras, and Web-facing building automation systems with no login.
New technology
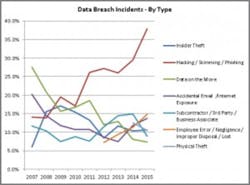
Hacking incidents are the most prevalent cause of data breaches and account for almost 38 percent of breaches. Hacking has dramatically increased since 2007. Source: Identity Theft Resource Center. All graphics courtesy of Unimin Corporation.
The future is about the Internet of Things (IoT). Security Consultant Indrajit Atluri imagines the following:4
You wake up each morning to the alarm from the fitness band on your wrist. Your movement triggers the band to send activity information to your iPhone, which communicates to a smarthome cloud service. The coffeemaker and lights switch on, the thermostat adjusts itself and the security alarm turns off.
As you suit up for the day, a drone delivers an order you placed online the previous night. You finish breakfast, courtesy of your WiFi-enabled toaster oven and remote start your car, locking the house via your smartphone as you head to work in a vehicle equipped with a state-of-the-art GPS that uses voice commands to get you to work. The piezoelectric sensors in one of the bridges on your daily commute trigger a stress alert to the monitoring tower that will automatically notify your autonomous car that is registered with the bridge toll service, about the bridge being closed down. This causes your car to recalculate and ultimately send you on an alternate route.
As the day ends, you decide on steak for dinner and use a phone app to preheat your smart grill so it’s ready as soon as you arrive home. You unlock the door with a touch, which pings the home network to turn on the hall light and adjust the house thermostat. After dinner, it is time for a little bit of television, and then you head to bed, for tomorrow brings a new day full of opportunities and challenges.
This might sound far fetched, but the truth is 6.4 billion connected devices are projected to be used this year, up 30 percent from 2015.5 Moreover, by 2020 4.3 connected devices per person will exist across the planet.6
Not the weakest link
In 2015, 160 breaches involved debit and credit cards in which less than 800,000 records were exposed. This pales in comparison to the 338 breaches involving Social Security numbers in which more than 164 million records were exposed. Source: Identity Theft Resource Center.
Precautions can be taken to ensure all parties are not the weakest link in the security chain.
Do not automatically trust email and only open attachments from known and trusted sources. For instance, notorious malware Cryptolocker can infect email attachments, so when an email is opened, it installs itself and encrypts files on the user’s computer. It then informs users of the encryption, and they can no longer access files on the computer. A message pop-up informs the user to make a payment for the encryption key to unlock the files.
Cryptowall, another ransomware, immediately scans and encrypts files on mapped network file shares. To mitigate the fallout from ransomware attacks, computer users should frequently run data backups. Other remedies include information technology departments limiting administrative privileges. Curbs on privileges connected with a general user’s account reduce the opportunity for ransomware to complete its mission.
High-risk activities have consequences. Mobile devices are the new attack vector because malware developers are -targeting smartphones and tablets. Users with smartphones who access pornography sites or content are particularly at risk. Android phones are easier to target than Apple iOS, which by default prohibits installation of non-Apple approved applications. Ransomware Kohler Trojan has targeted Android systems since 2014. Even Apple devices are not immune; an attack in 2014 locked both iOS devices and Mac computers. To mitigate smartphone compromise, users should only download and install apps from Android, Windows and iTunes stores where there is some degree of app vetting.
Be aware of the pitfalls of social and professional media because the Internet never forgets. Most information should remain private. Think twice before posting or transmitting personal details on Facebook, LinkedIn, Twitter, Instagram, Foursquare, PalTalk, YouTube and other media sites. Remember that employers are using social media to screen potential employees, and the five identifiers needed to impersonate someone online or over the phone include mother’s maiden name, date of birth, city of birth, name and phone number. These can be easily acquired through (but not limited to) wedding announcements, online people finder services, online resumes, and posting of major and minor life events. Nothing is private online.
Conclusion
The intent of this article is not to frighten people or to make them stop using the Internet but rather to enable business. The Internet revolution should be spread to promote smart and safe communication. For that to happen, everyone needs to be informed, to be an evangelist and to be positive.
Resources
- Identity Theft Resource Center, "2015 Data Breaches," http://www.idtheftcenter.org/ITRC-Surveys-Studies/2015databreaches.html, Jan. 4, 2016.
- Ponemon Institute LLC, "2015 Cost of Data Breach Study: Impact of Business Continuity Management," June 2015.
- Mandiant, "M-Trends 2016" https://www2.fireeye.com/rs/848-DID-242/images/Mtrends2016.pdf, February 2016.
- Indrajit Atluri, "The Rewards and Risks of Our ‘Smarter’ Future," InfoSecurity Professional Magazine, November/December 2014.
- Gartner, http://www.gartner.com/newsroom/id/3165317, Nov. 10, 2015
- Strategy Analytics, https://www4.strategyanalytics.com/default.aspx?mod=pressreleaseviewer&a0=5609, Oct. 14, 2014.
Jeffery Mayger manages Information security for Unimin Corporation. He holds Certified Information Systems Security Professional and Certified SCADA Security Architect certifications, and his experience includes SCADA systems and industrial controls. He may be reached at [email protected] or 203-966-8880.